Contact Us To Find Out More!
If you have any questions about MFA, IT Security and Support or just want to ask our friendly technical engineers some questions, contact us at [email protected] or call us on 1800 10 3000.

Moreover, AuthPoint™ goes beyond traditional multi-factor authentication (MFA) by incorporating innovative ways to identify users, such as with our Mobile Device DNA. With our large ecosystem of 3rd party integrations, this means that strong protection can be consistently deployed across the network, VPNs, Cloud applications – wherever it’s needed.
Even non-technical users find the friendly AuthPoint mobile app easy and convenient to use. Ultimately, itro’s AuthPoint is the right solution at the right time to make MFA a reality for businesses that desperately need it to block attacks.
Use of 2 or more authentication factors, from:
AuthPoint factors:

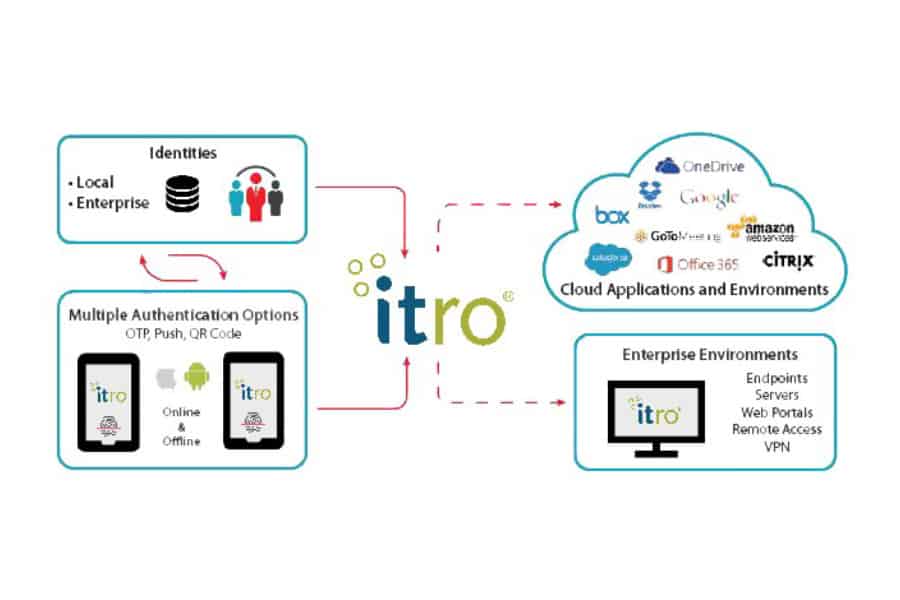
Multi-factor authentication (MFA) requires users to supply the information they know (username and password), and information provided on something they have, as well as other factors that can be associated with the specific individual. AuthPoint provides a highly secure MFA product using a push message, QR code, or one-time password (OTP); and our mobile device DNA matches the authorized user’s phone when granting access to systems and applications. Therefore, an attacker who clones a user’s device in an attempt to access a protected system would be blocked, since the device DNA would differ.
WatchGuard’s AuthPoint app allows users to authenticate right from their own phone! No need to carry key fobs or thumb drives; instead install and activate the AuthPoint app in seconds, and then use it to authenticate from a smartphone. It enables speedy push-based authentication as well as offline authentication using QR codes with the phone’s camera. The app is available in 11 languages and downloads free of charge from the AppStore and Google Play.
itro’s ecosystem includes dozens of 3rd party integrations with AuthPoint – allowing companies to require users to authenticate before accessing sensitive Cloud applications, VPNs and networks. AuthPoint supports the SAML standard, permitting users to log in once to access a full range of applications and services. In addition, the secure login feature provides online and offline authentication to Windows and Mac machines using the AuthPoint app.
If you have any questions about MFA, IT Security and Support or just want to ask our friendly technical engineers some questions, contact us at [email protected] or call us on 1800 10 3000.
For the past two years SME’s in Australia, and around the world, have been bearing the brunt of cyber-attacks, primarily because small businesses don’t see themselves as a target of value....
A recent report that analysed 360,000 BEC emails over three months has revealed the following top 12 most common subject lines used in emails targeting businesses......
Whilst I work with incredibly talented engineers, I am not one! In fact, when it comes to technology I call myself the “princess of darkness”. I’m surprised our engineers don’t turn and run the moment they notice me walking towards them with intent. “Got a moment for a chat?” ...
Did you get a bargain from the recent Black Friday sales? Or did your purchase not quite live up to its description? Imagine if a national survey was conducted to track customer satisfaction from online purchases made during peak sales times......












