
Law firms are losing millions to an email scam
Two Queensland law firms lost several million dollars promoting warnings from the Queensland Law Society (QLS).
An Attack Involves Two Phases
The method of attack doesn’t change – just which firm gets targeted! Please share this article with your team so they know what to look at for, and to strengthens your firm’s defenses. Jump to the end of this article to see extra security tips to help your team.
First Phase:
Hackers pretend to be a client enquiring about services from a law firm. A common approach is to pretend they are in the market to buy a house and are looking for conveyancing services. The objective of this conversation is get one of your employees to give hackers their log in details.
The hacker will indicate they are ready to proceed with your firm – to sign on as a client. They then send ‘confidential’ documents that require an employee’s login details to open them (refer below diagram). Once given, the second phase of an attack begins.
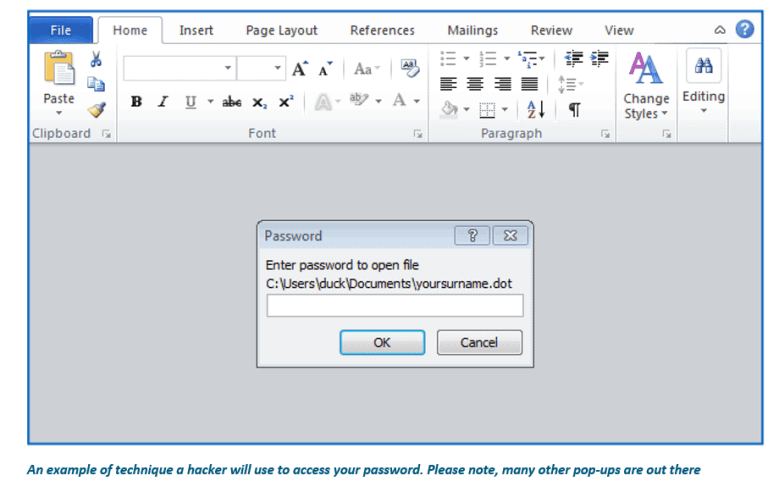
Second Phase: it’s all about patience!
Now a hacker has access to an employee’s email account, they will monitor that account and watch for information about settlements and outstanding payments or deadlines.
This is where the hacker becomes incredibly cunning. Once details on a payment deadline have been identified, a hacker then will send an email to the relevant client masquerading as the firm owed payment, reminding a client of their due payment date. Except! They provide banking account details for their account, not your firm’s trust account.
The common practice of clients waiting to pay on a due date unwittingly helps hackers. A client, aware a payment is due soon, is unlikely to question a reminder email allegedly sent from the practice they engaged. They simply need to copy the account details and make the payment. Nice and easy! Until your Accounts department starts chasing payment, no one will even realise an attack has been successfully carried out – and your money is gone!
Tips to avoid similar attacks:
- Do not ever provide login details when opening an attached document from an untrusted source
- Pull back if a prospective client is asking for email credentials
- Two-step authentication is vital – even if an employee provides their log in details to a hacker, systems are in place to block the hacker from accessing any data
- Encourage your clients to call and verify trust account details before transmitting funds
Tips on how to spot emails as illegitimate:
- Non-personalisation or incorrect personal details
- Suspicious or hidden email address, therefore, always check domain addresses because Netflix will only ever send an email from a domain of @Netflix.com
- Misleading hyperlinks. Before clicking any links, hover over it and check the domain it is linking you to and if they look suspicious do not click them and instead refer to the company’s website

