Display Name Spoofing, Are You Next?
Have you heard about ‘Display Name Spoofing’?
Recently some clients are finding themselves victim to Display Name Spoofing. This highly targeted spam attack passes through mail-filtering solutions, unlike other spam emails. It involves mail sent from a registered email address on a valid domain (EG: [email protected] or [email protected]), but with the display name set to a key contact or partner of a user within the recipient organisation.
What this article will run you through:
- How this scam works
- Why is it bypassing anti-spam mail filter solutions
- What itro is doing to prevent display name spoofing
- What you can do to prevent email spam attacks
- Tips on spotting an email as illegitimate
How:
The email displays the name of a key contact or someone you deal with regularly BUT the email address is incorrect. The problem is people rely on the display name rather than looking or checking what the actual email address is. Additionally, Outlook and most other email platforms show the display name over the email address for user friendliness.
Unfortunately, social media has created an avenue for scammers to source information about your company within seconds. It is simple to impersonate you or a colleague as scammers can find out personal information including your name, where you work, email, and job position within minutes.
Their goal:
To mislead a user, by impersonating a key contact or any user within the organisation, into transferring money into an account or infiltrating your systems and data.
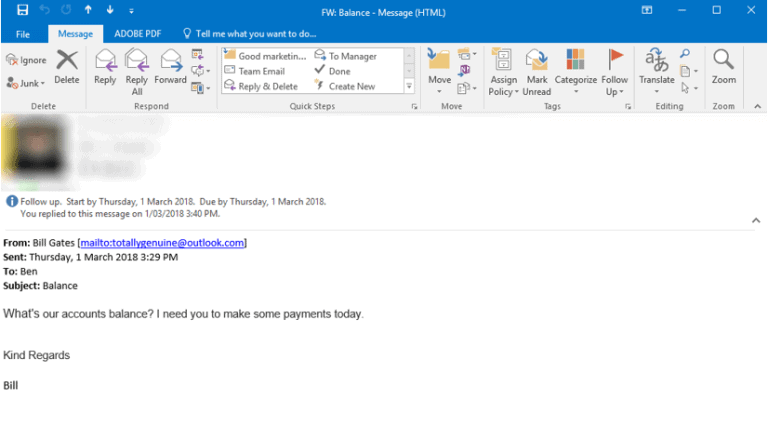
For example, as you can see below, although the display name is Bill Gates the email address does not belong to Bill Gates:
How is it bypassing my anti-spam mail filtering solution?
The sender will appear legitimate upon casual inspection. This is because Outlook and some other email clients will show the display name over the email address for user-friendliness).
These emails will make it past the filter because they contain no suspicious content, only vague one line sentences requesting further information regarding an account or invoice. Some of these attack types will still attempt to deliver the usual trojans/crypto via a compromised URL or document attachment).
Once a user has responded to this vague query, it will be followed up with a request for payment to a certain account.
What itro is doing
If you are using Office 365 through itro, you may notice the below notification when you open some received messages. itro will display the alert when our systems detect possible spoofing.
This is one of the benefits of using Office 365 through itro.
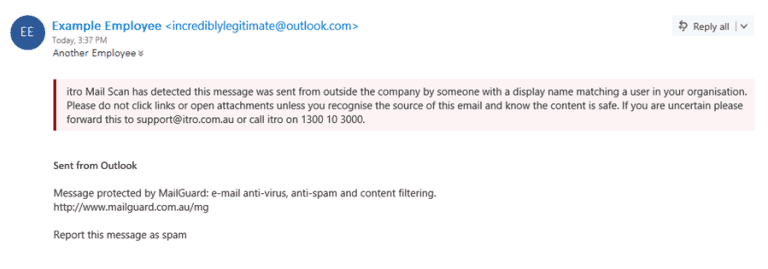
If you see this message, you should carefully consider whether to open the email or any attachments, if in any doubt contact itro service desk by phone and someone will look into it for you.
What can you do?
The method of attack is not changing – just which firm they target! Please share this article with your team so they know what to look at for, and how to strengthen your firm’s defences with the below.
- Implement verbal clarification to any email money requesting a transfer for large sums of money
- If you receive an email requesting for a significant money transfer, call or text the person and confirm its legitimacy.
- If you’re unsure, call itro to check the email’s legitimacy
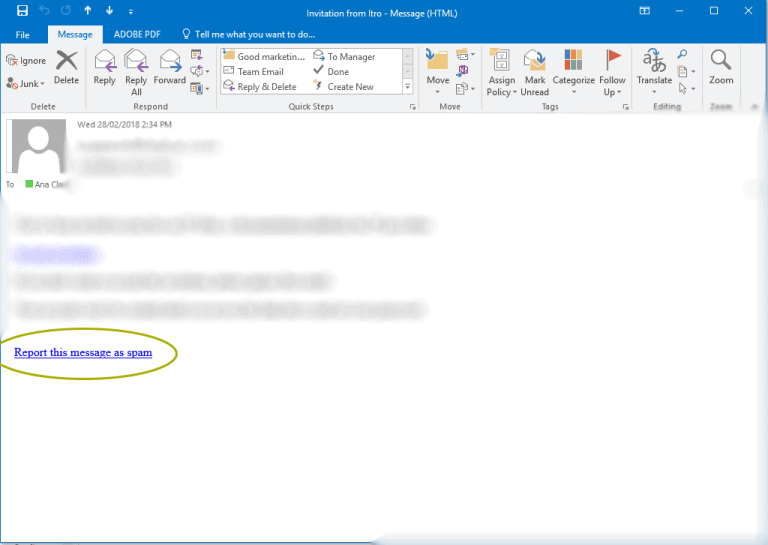
- Report the message as spam (if you are using itro Mail Scan). See below:
Tips to spot an email as illegitimate
- Suspicious or hidden email address. Always check domain addresses because itro will only ever send an email from a domain of @itro.com.au
- Non-personalisation or incorrect personal details
- Misleading hyperlinks. Before clicking any links, hover over it and check the domain it is linking you to. If they look suspicious do not click them and instead refer to the companies website.

