
Simple Ways Organisations Get Hacked
Preferred Targets
Deloitte reports Australian financial institutions are in the highest risk category for cybercrime across Asia Pacific.
Why Is Australia So Bad for Cyber Crime?
1. Our ICT Infrastructure Is Better
The interconnectedness of Financial systems and devices globally and regionally increase the risk of multiple Institutions being affected or infected from a single origin cyber-attack.
‘Generally, businesses operating in countries that have more advanced ICT infrastructure and a bigger digital economy face greater cyber risks. For example, Korea, Australia, Japan and Singapore have been found to be nine times more vulnerable to cyber-attacks than other Asian economies.’ (Cyber Regulation in Asia Pacific–Deloitte)
2. Lack of Dedicated IT Security Specialists and Cyber Professionals.
Getting the right people with the right skills is expensive, and difficult to acquire.
3. Poor Internal Controls + Social Engineering = Problems
Whilst Financial Institutions (FI’s) are good at having strategies for managing external cyber risk factors, a lack of understanding on the importance of controlling internal functions is creating an uneducated or lazy approach amongst employees on how to limit cyberattacks.
Social Engineering – A Nasty Abuse of Trust
Employees are being tricked into giving away confidential information or money to someone they think they know (known as ‘social engineering’).
Cyber criminals only need basic information on your company structure or employees to engineer a targeted email attack. This year The Australian reported a senior Banking executive as saying, “Hackers are now heavily researching social media accounts of business leaders and using their airport check-ins and family holiday Instagram pictures to customise their emails and make their approaches more personalised.”
All it takes is one email…
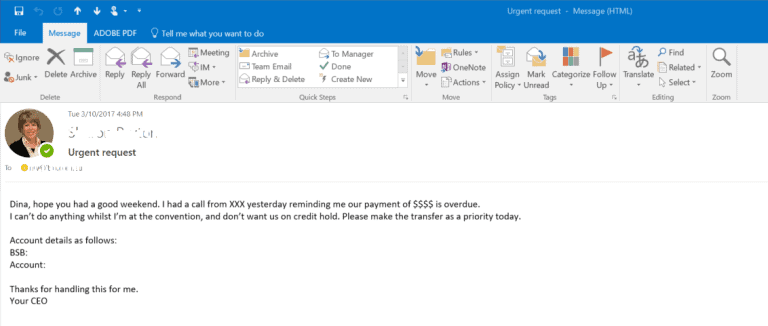
One Scam You Need to Act Against Immediately
The Australian Criminal Intelligence Commission’s (ACIC) recent report into organised crime shows just how dangerous business email compromise (BEC) is to business!
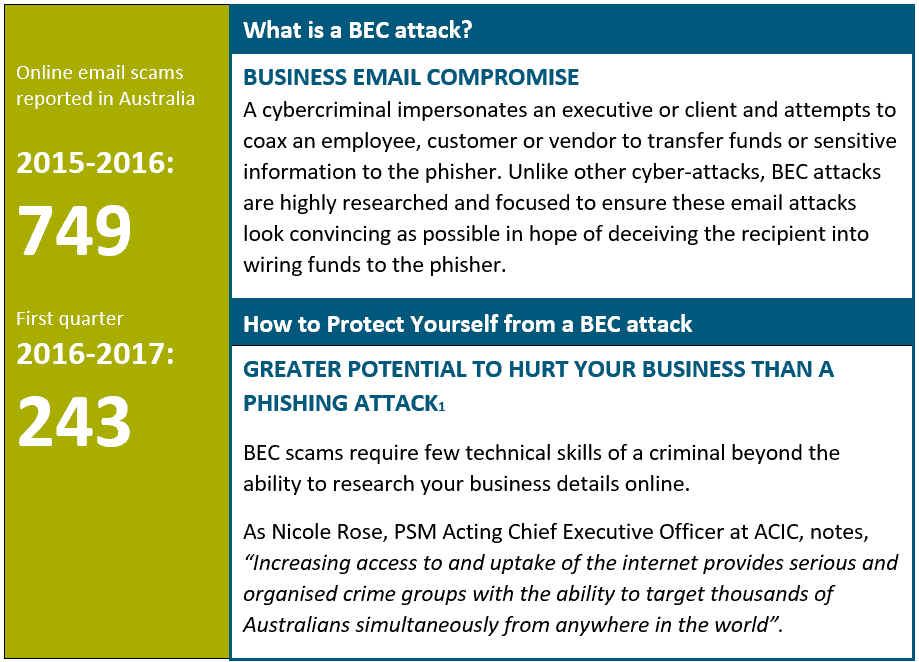
Reduce Your Risk
1. Email Filters
Good email filters[2] interrogate mail before delivery in two ways:
- By qualifying the legitimacy of sender details; and
- filtering through content of an email.
NB: Even good email filters depend on being configured correctly for maximum security. Engage an IT Provider with proven experience in configuring and proactively maintaining email filters to evolving security solutions.
2. Employee Education
Teach your teams how to block cyber-attacks, and reward their efforts. Happy employees make great security advocates. Simple checkpoints to implement include:
- Sender details. Check an email is coming from a legitimate contact. For example, a bank is NOT going to send you an email via Hotmail ([email protected]). Check the sender’s name as well as the domain extension. It’s an easy, effective way to avoid opening malicious emails.
- Opening Files. Teach your team to check files attached to emails before opening them! If in doubt, encourage them to seek advice from you, a manager or your IT Provider. Files that execute commands, such as
- program files (*.exe)
- batch files (*.cmd and *.bat); and
- script files (*.vbs and *.js).
File types that allow for embedded script operations, such as:
- Microsoft Access files (*.mdb);
- macros in Microsoft Word files (*.doc); or
- in Microsoft Excel files (*.xls).
And for MAC users, be cautious with:
- C Shell Script files (.csh);
- executable files (.osx);
- images (.tiff); and
- iOS application files (.ipa)
- Money Transfers: Encourage your Accounts team to ring and verbally qualify any unexpected email requests for money supposedly sent by a senior team leader or internal department before making a transfer. Even if a follow-up call causes annoyance, that is a far better option than having to tell management funds were unwittingly given away!
- Financial Records: Emails requesting financial records for a business partner, client or agency be updated must always be treated with caution! Have policies in place that require all such email requests be qualified before being actioned.
Have the Right Team to Manage Your Cyber Security
Getting the right people with the right skills to manage your internal systems can be expensive and difficult to source. If you have limited resources, a practical way to implement a resilient and proactive cyber security framework is to engage itro’s team of IT engineers.
If you would like to know more about email filtering, firewalls or how itro can configure your technology to maximise your protection, please call Lucas or Matt now on 1300 10 3000.
Not ready for a sales conversation? Check out our pricing options here
[1] Refer to ‘Hundreds of businesses are being hit by this crafty cyber attack that’s more devastating than phishing scams’, by Dominic Powell, published by SmartCompany-Technology
[2] For more information on email filters and how firewalls work read: ‘5 Steps to Protect Your Data from Theft’ and ‘What is a Firewall and why do we need it?’.

