
Phishers Are Targeting Office 365 Again
Phishers have a new trick up their sleeve, they are checking the credentials entered into a spoofed login page in real time and the victims are redirected to their real Office 365 inbox!
Researchers have not seen this method used before and it is concerning!
How do they pull this off?
Firstly, the send you a fake email supposedly coming from Microsoft:
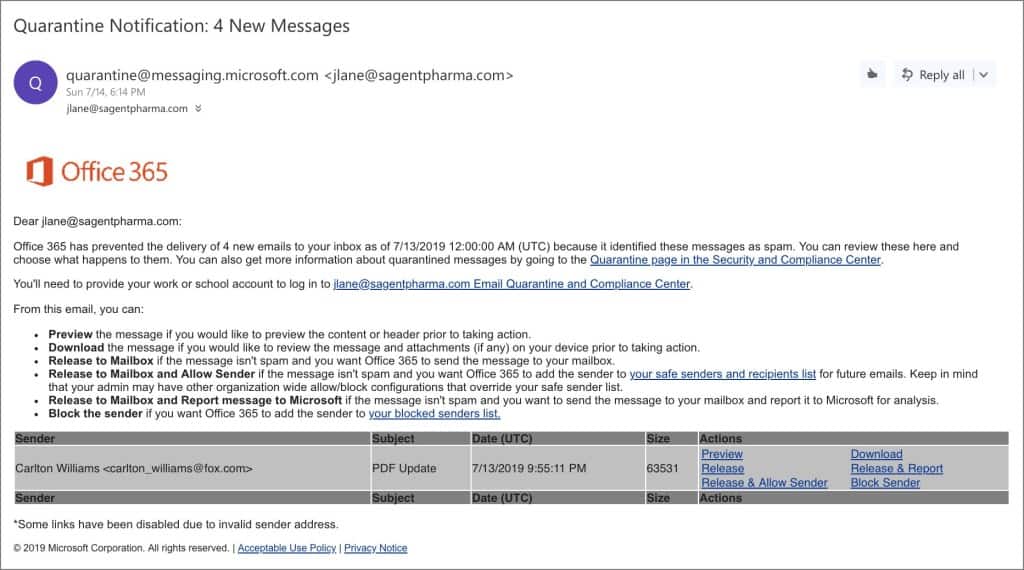
All the links in this email point to a fake Office 365 login page, located in the Microsoft Azure Blob and accessible via a windows.net domain (complete with a valid Microsoft SSL certificate).
The log in page includes a script that validates the Office 365 credentials by triggering a back-end IMAP client that tries to login real-time.
If login is successful, the hackers immediately start syncing the victim’s emails to a remote client via IMAP protocol while the victim’s browser directs to the real Office 365 portal. This provides a genuine ‘conclusion’ to the attack, so the victims aren’t aware of the account compromise.
If the login fails, then the victim is shown an error page like they would on a legitimate Office 365 site. This neutralises the advice often given to users to try entering fake credentials if they believe a login form might be fake.
Lastly, the phishing victim might not realise their account has been compromised for quite a while, leaving the attacks free to make cover changes that might work in their favor.
Protect Your Accounts And Your Data
Enable MFA and disabled IMAP access if possible as it can be exploited to bypass MFA. If you don’t know how to do this yourself, contact itro on 1800 10 3000or email [email protected] to ask about itro Mail Scan that can help stop phishing emails like this coming through your inbox to deceive you.
All genuine Office 365 login pages can only be found on the microsoftonline.com domain.

