itro Device Protection and Cyber Security
Keep your devices cyber safe online, 24/7
Keep your devices cyber safe without even thinking about it.
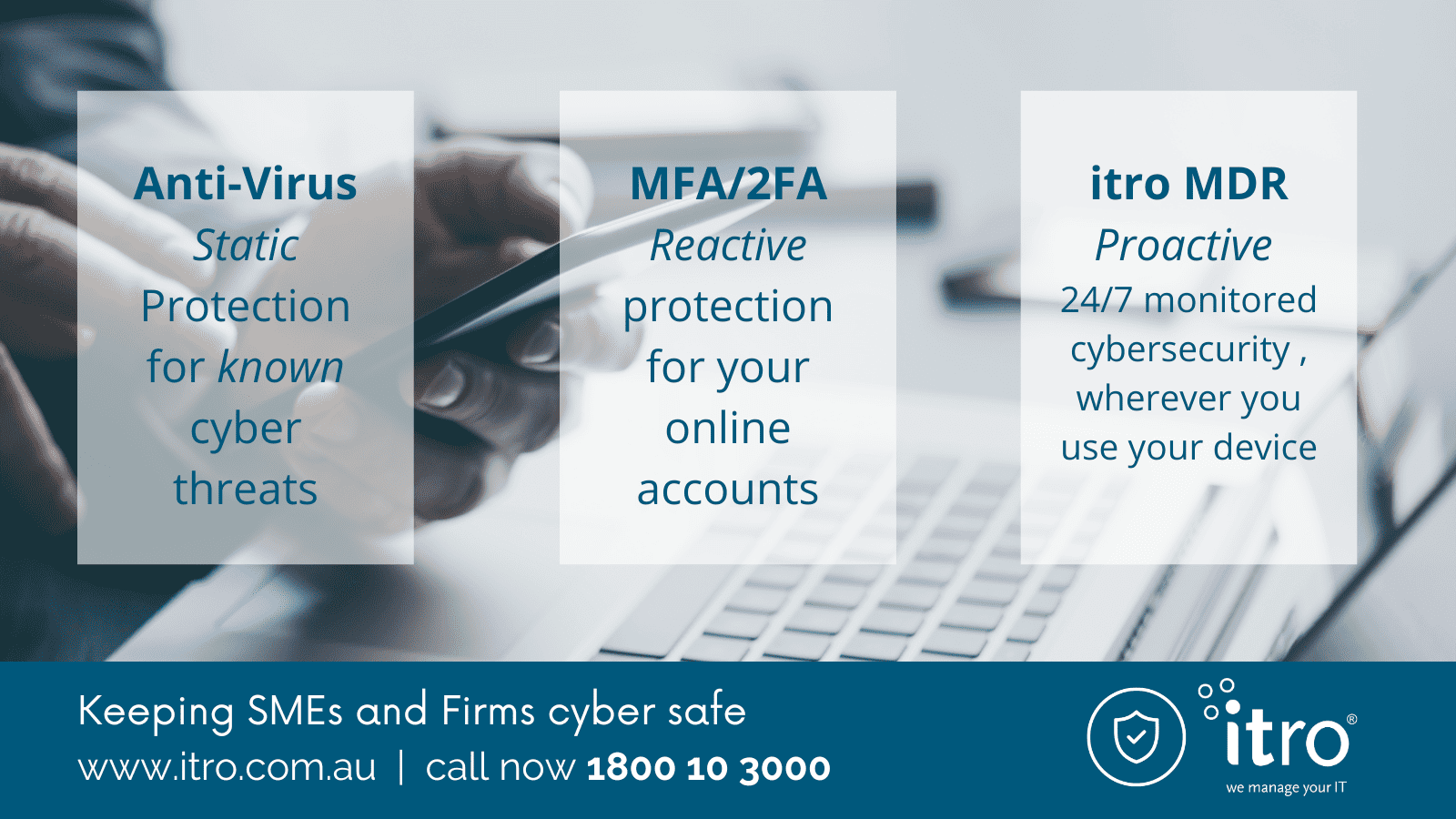
itro MDR (Managed Detect & Respond) detects and responds to known and emerging cyber threats, plus any activities identified as ‘unusual’, that are activated through one of your business endpoints. Designed for business professionals, our premium cyber security service shields your devices – physical and virtual – from hidden cyber threats 24/7.
Whether you work in a protected office environment or remotely, at a conference or client site, in a transit lounge or your favourite coffee shop, itro MDR proactively keeps you cyber safe!
itro MDR
Proactive device security for remote working needs
itro MDR (formerly known as Endpoint Protection) embeds monitored cyber security into your devices, protecting you and your team wherever you work – your office, home or any other remote location.
How does it work? Once subscribed, your device is monitored 24/7 by our Security Operation Centre (SOC).
Whilst some managed cyber security platforms rely solely on AI functionality, itro MDR is a ‘live system’ that combines human insight with AI technology. Whatever time or day an attack or unusual activity occurs, our Security Operations Centre will detect and immediately respond to real and perceived threats. This means no time is wasted blocking an attack, wherever it originates from. itro MDR keeps your devices safe as it monitors all online access points to your devices, including ‘trusted’ and ‘untrusted’ applications, and third-party partners.
We highly recommend you subscribe to itro MDR if you want premium, business-grade transportable cyber security for your team and devices.
Get your free cyber security consultation started today
Scroll down to see pricing
What is an endpoint?
An ‘endpoint’ is any physical or virtual device you use as an entry point to access your network and conduct business. This includes devices such as desktops (Windows or MAC), laptops, tablets and servers. They enable you, your team, invited guests or malicious hackers to connect and access your emails, data, other devices and infrastructure across your network and in the cloud.
Why is protecting your devices so important?
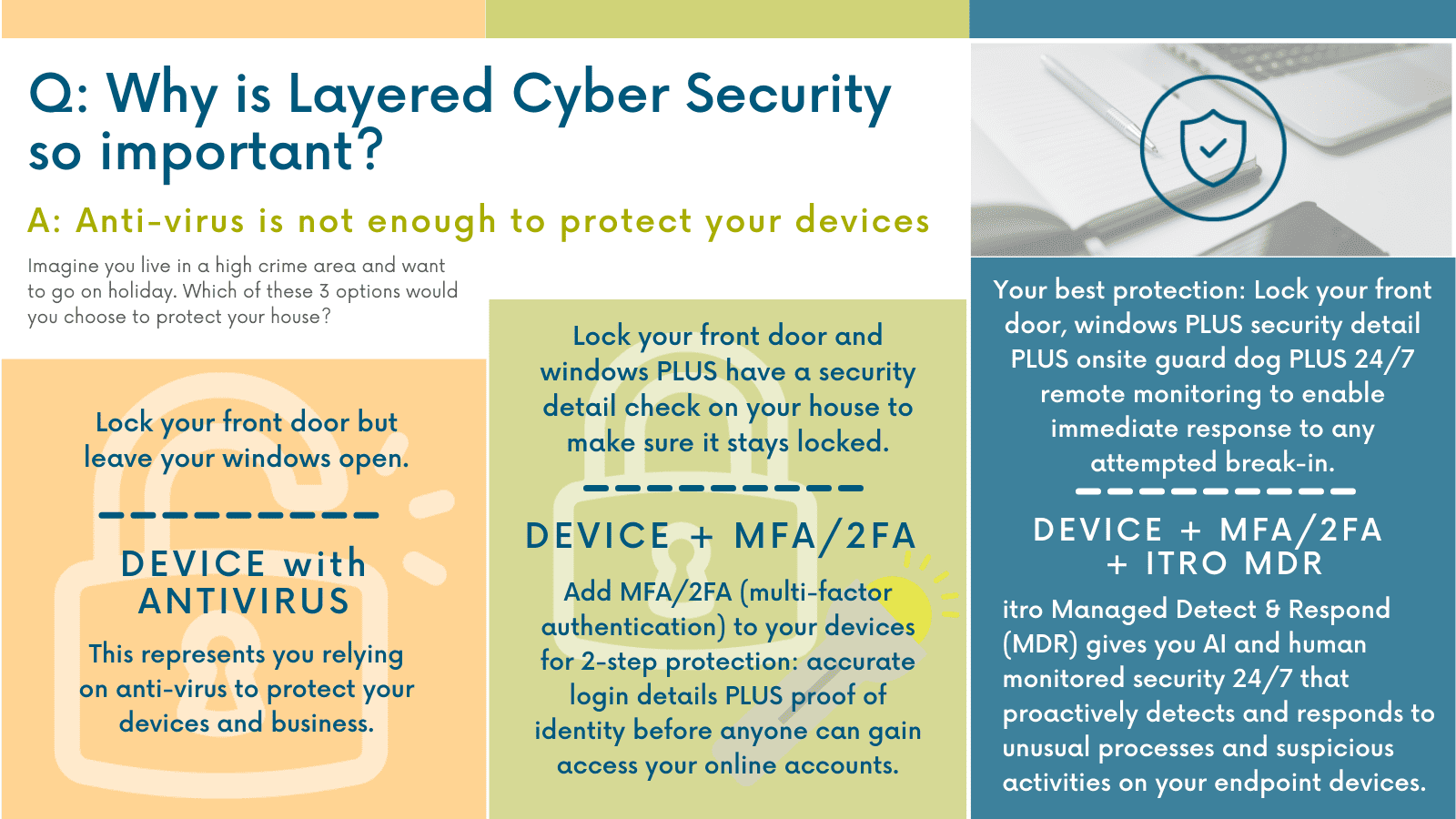
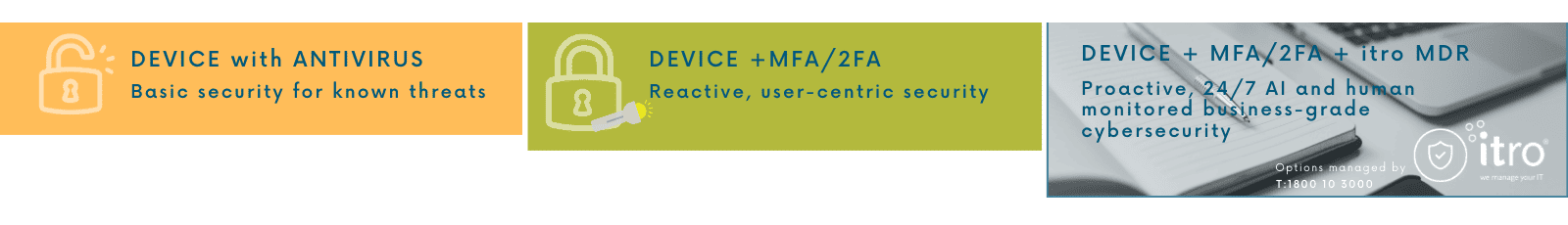
Whenever you use a device to go online you are opening a two-way ‘door’ between your device and the internet. Without layered security measures, working online is akin to leaving the front door to your office or house open. You can come and go whenever you want – as can anyone else.
When you work within a well-protected office environment with firewalls and proactive cyber-security protocols your risk of cyber attack is very low.
However, stand-alone devices used away from your office, especially ones with out-of-date software or using antivirus as their only defence, are easy targets. BYO devices add another level of risk and danger to your business, as they are essentially a foreign endpoint with unvetted apps and software connecting to your network.
Think about your average working day. How often do you go online to download or upload files, connect with others, research, read your emails, click on links, etc? Each time you connect to the internet, you are exposed to cyber risk. When you work at your office you (should) have the added protection and security of your company firewall, but what happens when you work away from your office? What layers of cyber security do you have at home? What do you use to connect and work online when you visit other business premises, a client or work from your favourite café?
Pricing
With any of itro’s Managed Support Plans, you can add itro MDR for:
$10
per endpoint, per month
Call us now on 1800 10 3000 to speak with one of our friendly Technical Engineers for more information about our Support Plans, MFA and itro MDR or email [email protected]. itro gives small to medium businesses and Firms the expertise and security they need to stay cyber safe.
Key benefits for your Business
On-demand security operations
Cyber threats and hackers target SMBs and sole Practitioners as well as big enterprises and Firms, leveraging the same tactics. We provide a security operations center (SOC) that scales protection with your business, providing the staff necessary to drive threat remediation.
Simple deployment, always-available threat coverage
itro MDR detects known and unknown threats leveraging the latest behaviour-based technology, regardless of where your endpoints are deployed (office, home, airport, café, hotel, etc.).
Next-gen threat detection and remediation
Our solution incorporates patented threat identification and remediation technology, to fully protect desktop and server environments.
itro does it better with:
- 24×7 SOC service
- Immediate risk identification
- Effective response, quick remediation
- Ransomware rollback
Key features of itro’s proactive, business-grade device security
Complete 24/7 SOC Services
Implement advanced operations without the need for in-house security expertise. The complete SOC analyses quarantines applications and files, reducing false positives and ensuring comprehensive protection. itro takes care of the challenges of your cyber security leaving you to focus on your business.
Threat Detection
Our solution rapidly recognises thousands of viruses and malware attack variants, including crypto mining attacks as well as the root causes of these malicious behaviours, by quickly identifying and diagnosing corrupt source processes and system settings.
Response and Remediation
When malicious behaviour is detected, itro MDR quickly rolls back files to previous safe versions by tracking changes in your devices and restoring them to an acceptable risk state.
Next-Generation Endpoint Security
itro MDR utilises the patented SentinelOne platform for its unique malware detection and remediation technology. This solution incorporates the Security Industry’s most innovative prevention measures, providing visibility into the root causes and origins of a threat, reversing malicious operations and remediating them quickly.
Subscribe to itro MDR now by ringing itro on 1800 10 3000 or email your request to us: [email protected]
Related articles:
8 Steps to Protect Your Business From Cyber Attacks – itro
SMBs Spend Less on IT With These Top 3 Tips – itro

