MFA and Cyber Security
Multifactor authentication (MFA/2FA) is a cyber security tool that protects your apps and online accounts from being accessed without your permission. It stops others who know your login and password, or have stolen them, from getting into your online accounts.
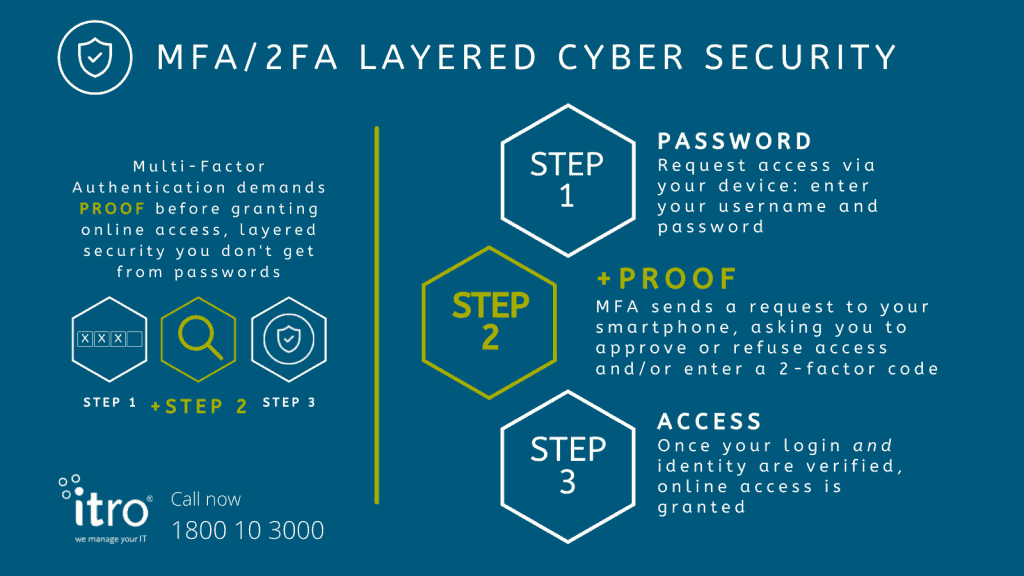
How does MFA/2FA work?
MFA protects you by adding another step* to your login process. Having your login name and password is not enough to access MFA-protected accounts.
Once your login and password are entered, MFA sends a request to your smartphone to make sure it’s you asking for access. You will need to approve or refuse access (YES/NO), or enter a unique 2-factor code MFA sends to your phone.
*Another step: Multifactor, or Two-Factor, Authentication (MFA/2FA) adds an identity check to your standard login process.
Protected when your login and password get stolen
If your username and password gets compromised or stolen, MFA protects you with it’s unique two step proof of identity. And MFA gives you get an extra bonus. Because MFA alerts you to all login attempts, you will know instantly if a malicious attempt is being made to access your accounts. If it’s not your request, then someone else knows and is trying to use your user name and password. You need to change your login details ASAP.
MFA has become such a vital layer of cyber security, tech-giants like Google will make it a compulsory add-on for their account holders. Scroll down to see Mark Risher, Director of Product Management, Identity and User Security, comments on why Google has made this decision.
Is MFA difficult to use?
In talking to others, I find a big concern about MFA is that it will make your login process too hard. Speaking from experience MFA is easy to use, especially if you always have your mobile phone with you. Yes, MFA does add another step but that’s what makes it difficult for hackers or disgruntled associates to break into your online accounts.
Is MFA worth the trouble of adding another step to your login process? Absolutely! Your online accounts are double-guarded, and its easy to use. See how easy with our illustrated info sheet itro-MFA-Info-Brochure.pdf
Get your free cyber security consultation started today
Is MFA ‘unhackable’?
Turning on two-factor authentication makes it a lot harder for hackers to access your online accounts and apps, but not impossible. A particularly determined hacker who already has your username and password could steal your phone or spoof your phone number to gain access to your messages to intercept MFA requests, but that would be a very targeted attack.
Passwords aren’t enough
The traditional login process of giving your user name and password is not enough to protect you from cyber-attacks or your apps and online accounts being maliciously accessed.
The Australian Federal Government is so alarmed at the steady rise in cyber-attacks on Australian businesses and citizens it is actively promoting you to use multifactor authentication to increase your online security. See ‘Implementing Multifactor Authentication’ by ACSC (Australian Cyber Security Centre www.cyber.gov.au).
Relying on passwords for your cyber security is like locking your front door but leaving all your windows open. MFA, on the other hand, locks the ‘doors and windows’ on your apps and online accounts and acts like a guard dog ready to respond if bad guys find your spare keys. Multifactor authentication is a must to keep you cyber safe.
(MFA is one of two key, layered security measures recommended by ACSC to protect your online data and accounts. Each layer gives you a different level of protection. MFA gives you the security of reactive protection for your online apps and accounts while the second layer gives you proactive^ 24/7 monitored security that works wherever you use your device. ^Please refer to ‘Have Business-Centric Cyber Security’ in this article for more details.)
Protect your business from cyber threats
Promote a ‘security culture’
With random acts of cyber-crime endemic and targeting both consumer and business users, it’s important you and your team develops a ‘security culture’ when it comes to all online activities. Always pay attention to suspicious emails and alerts; check links are legitimate before you click; and before transferring money or changing account details always take the time to directly phone whoever is supposedly making a request; and remain vigilant.
Have layered, business-grade cyber security
All users should use MFA/2FA for the added protection it gives your online accounts and data. Is adding MFA enough to protect businesses? Whilst it gives you better protection than passwords and antivirus do, the best defence against cyber threats is having layered security measures that work together to protect your devices, apps, online accounts and data. itro highly recommends you initiate 5 essential steps to protect your business from cyber threats:
- Stop a threat from reaching your ‘front door’
- Don’t let it through your ‘front door’
- Stop or slow down the spread if it gets into your network
- Perform regular data backups
- Keep up with software updates.
Whilst MFA and antivirus help you with the first two steps, they do not alert you or stop your systems from being comprised if a hacker gains access to your online accounts or data. However you can be alerted and stop, or slow, the spread of a cyber attack by integrating another layer into your IT security measures – proactive 24-7 monitoring of all your internet enabled devices with itro Endpoint Protection.
When you subscribe to MFA and itro Endpoint Protection through one of itro’s Managed Support Plans you gain the peace of mind of proactive 24/7 cyber security, regardless of where your team works from – either within your protected office environment, offsite or remotely. NB For more information of the role antivirus plays in your cyber security, please read my article, ‘Antivirus and Cyber Security’.
Get your free cyber security consultation started today
Don’t rely on passwords
Why are passwords not enough to protect your online accounts and apps? Because passwords are surprisingly easy to crack. For starters, people are still using obvious passwords such as ‘123456’ or ‘password’. As of 2020 ‘123456’ is still the world’s most commonly used/easily abused password. That fact makes cyber security experts around the world tear their hair out as they struggle to understand why people keep making the same bad password choices year in, year out. But let’s face it, most of us have enough to think of without adding difficult-to-impossible-to-remember passwords to our lives! Sadly, dishonest people and hackers count on that!
Technology to crack your passwords
The second reason passwords are easy to break is technology! Software is available online to anyone who wants to crack passwords. Google ‘breaking/cracking passwords’ to get an idea of how much information, videos and help is available online for people wanting to break passwords. It doesn’t make for comfortable viewing!
This is why you should only ever use complex passwords to protect your online accounts. (NB Using a Password Manager app, such as LastPass, helps you generate complex passwords and store them in a secure online account you can access, using MFA, from your device or smartphone). However, complex passwords in themselves aren’t a guarantee your online accounts won’t get hacked. They protect you from opportunistic attacks and will delay hackers who use technology to crack your passwords, but they are not infallible.
In summary:
- MFA gives you the security of reactive protection for your online apps and accounts.
- itro Endpoint Protection gives you proactive 24/7 monitored security that works wherever you use your device.
For more details on itro Endpoint Protection, please read my article, ‘Keep your devices cyber safe online, 24/7.
If you have any questions in relation to cyber security, MFA, itro Endpoint Protection, or are concerned your current IT security measures are inadequate, please call itro now on 1800 10 3000. Our engineers will happily answer your questions and you can request our free IT consultation.
Related articles:
How Important is Cyber Security?
SMBs Spend Less on IT With These Top 3 Tips – itro
Why Google and tech giants are making MFA/2FA compulsory
On World Password Day (6 May 2021) Mark Risher, Director of Product Management, Identity and User Security, Google, announced Google LLC is going to make MFA compulsory for all account holders under the banner, ‘A simpler and safer future – without passwords’. Why? Mark Risher answers:
“You may not realize it, but passwords are the single biggest threat to your online security – they’re easy to steal, they’re hard to remember, and managing them is tedious…
Unfortunately, even the strongest passwords can be compromised and used by an attacker – that’s why we invested in security controls that prevent you from using weak or compromised passwords…
Soon we’ll start automatically enrolling users in 2SV (Google’s two-step verification process) if their accounts are appropriately configured.”
I find this really interesting. The company I work for, Melbourne-based MSP itro, along with software developers and cyber security experts globally, has been encouraging users and clients to adopt layered security measures for a number of years, yet response from businesses and Firms has been slow. Unfortunately a lax attitude and/or misunderstanding of the magnitude of cyber threats affecting businesses has created a minefield of hidden online dangers. How? We live in the age of The Internet of Things (IoT), with billions of physical devices around the world collecting and sharing data. Whilst your business or Firm may have implemented key steps promoted by the Australian Government to protect your business from cyber threats, your affiliated suppliers, clients, contractors or stakeholders may not. Their compromised systems can be used by hackers as ‘backdoors’ to your online business and data.
Knowing the risk is enormous, and growing, Google has chosen to start enforcing baseline security measures for their account holders by making two-point, or multifactor, authentication mandatory. What does that tell you? That Google LLC, with all its vast technical and people IT resources, is choosing to mandate use of MFA for its connected subscribers? MFA is a must for any business or Practice wanting to protect itself from online cyber risks.

